There are many types of hashing algorithm such as Message Digest MD MD2 MD4 MD5 and MD6 RIPEMD RIPEND RIPEMD-128 and RIPEMD-160 Whirlpool Whirlpool-0 Whirlpool-T and Whirlpool or Secure Hash Function SHA-0 SHA-1 SHA-2 and SHA-3. The size of the hash is 128 bits and so is small enough to permit a birthday attack.
Hash algorithms have been around for decades and are used for applications such as table lookups.

How to choose good hash algorithm. Adapting Knuths suggestion c to be fraction of the form s 232. Hashing algorithms are mathematical functions that convert data into fixed-length hash values hash codes or hashes. SHA-1 gained widespread use and acceptance.
I know there are things like SHA-256 and such but these algorithms are designed to be secure which usually means they are slower than algorithms that are less unique. In the universe of the cryptocurrencies the most used hashing algorithms are SHA-256 and X11. The most important thing about these hash values is that it is impossible to retrieve the.
Nicehash How To Choose Algorithm University. Nice hash will pick the most profitable algorithmEven if the algo you want to use is faster the value of the currency might be such that the miner is choosing. Suppose k 123456 p 14 m 214 16384 and w 32.
There are many different types of hashing algorithms. SHA-256Specifies the Secure Hash Algorithm SHA-2 with the 256-bit digest. Since youre hashing files using a php function like md5_file does look tempting.
RSAs strength is directly related to the key size the larger the key the stronger the. Multiply the w bits of k by floorA 2 w to obtain a 2w bit product. Extract the p most significant bits of the lower half of this product.
MD2 MD5 SHA and SHA-1 are examples of hashing algorithms 4. Choose m 2 p. For a hashing algorithm to be considered secure it should have double the amount of calculations required to solve it in a feasible time.
Example good uses include hash dictionaries. SHA-384Specifies the Secure Hash Algorithm SHA-2 with the 384-bit digest. This is a good practice to put in place every time you add a new hashtag to your repertoire.
Gary Lee in Cloud Networking 2014. SHA-1 creates 160-bit outputs. Computers are getting faster all of the time and so more advanced hashing algorithms are being developed all the time.
This is actually a suite of hashing algorithms. What are Hash Functions and How to choose a good Hash Function. The output of the hash algorithm will be a pointer into a table where the persons information will be stored.
When choosing hash algorithms and key lengths one needs to take into account the current landscape. The suite contains SHA-224 SHA-256 SHA-384 and SHA-512. I want a hash algorithm designed to be fast yet remain fairly unique to.
Choose one type of hashing algorithm and data of any character count put through the system will emerge at a length predetermined by the program. Digital signatures are composed of two different algorithms the hashing algorithm SHA-1 for example and the other the signing algorithm RSA for example. Using crc32 might at first seem like a valid option because it was developed with the intent to generate hashes to check file integrity.
Over time these algorithms or the parameters they use need to be updated to improve security. SHA-1 was actually designated as a FIPS 140 compliant hashing algorithm. Hashing and Hash Functions 3.
The SHA series of algorithms stands for Secure Hash Algorithm they were designed by NIST. The output hash value is literally a summary of the original value. But it really is quite old and because the hash itself is only 32bit it stands to reason that the.
This video walks through how to develop a good hash function. Then key s 327706022297664 76300. Education 5 days ago level 1.
Is likely to work reasonably well. When running NiceHash Miner is connected to NiceHash platform and NiceHash open hashing power marketplace. SHA-1 is one of the main algorithms that began to replace MD5 after vulnerabilities were found.
The following SHA-2 options which are even more secure are available for IKEv2 configurations. Advanced encryption standard AES is the replacement for DES. For example you can use a persons name and address as a hash key used by a hash algorithm.
Education 5 hours ago Nicehash Switch Algorithm UniversityEducation 8 hours ago rNiceHash - Can you change the algorithm of your current. There are 4 key components involved in hashing. A sqrt5-12 06180339887.
The algorithm does just one thing compress data and nothing else. You need to do a little bit of research on how hash algorithms are currently standing up to collision attacks and what key lengths are acceptable. The keys to remember are that you need to find a uniform distribution of the values to prevent.
The hash table is a storage location in memory or on disk that records the hashed. Which hashing algorithm is best for uniqueness and speed. 3 of The Art of.
Buyers select the algorithm and the speed while users or miners running the NiceHash Miner software fulfil that order by mining hashing - providing computing power to. Choose one of these if you want to implement the NSA Suite B cryptography specification. Using banned hashtags can cause a drop in engagement as your use of legitimate hashtags might also become less effective because you could be dropped in the algorithm.
Is a good choice see Knuth Sorting and Searching v. Due to the avalanche effect even a minor change in the data to be encrypted will. But possibly because md5 has been shown to be unsafe PHP comes with a sha1_file function.
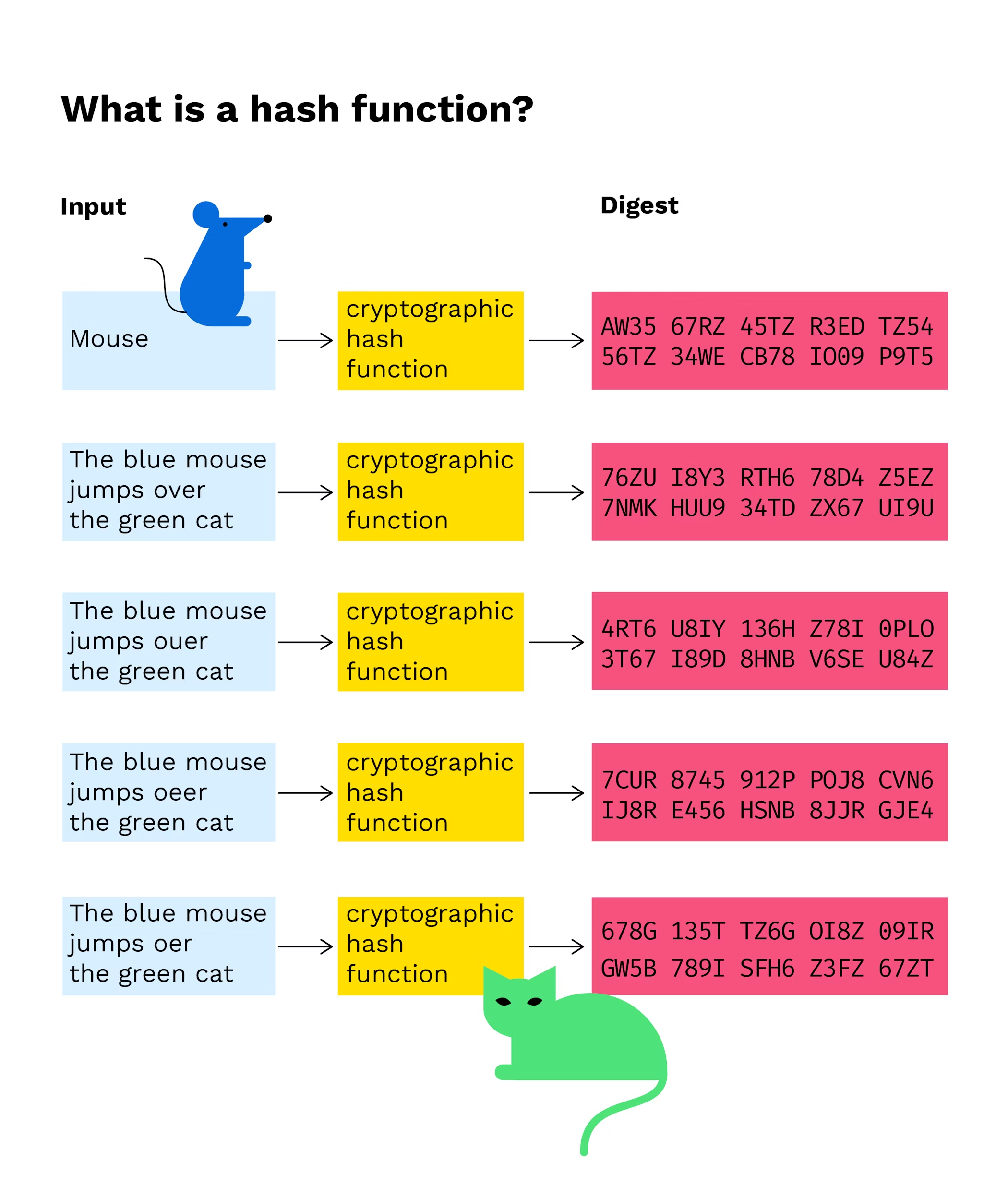
What Is A Hash Function In A Blockchain Transaction Bitpanda Academy
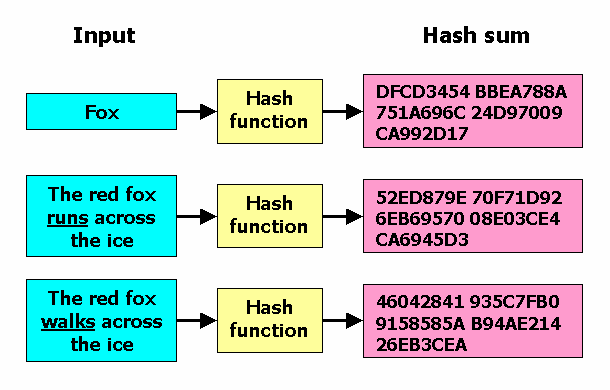
Md5 Vs Sha 1 Vs Sha 2 Which Is The Most Secure Encryption Hash And How

Hash Function In Cryptography How Does It Work Infosec Insights

Hash Function An Overview Sciencedirect Topics

Hash Function In Cryptography How Does It Work Infosec Insights

Hashing Algorithm Overview Types Methodologies Usage Okta

Cryptographic Hash Function In Java Geeksforgeeks